How to Scale Your Vendor Security Response Process
In the course of the third-party risk management (TPRM) process, vendors need to disclose their security posture, including policies, insurances, certifications, audits and operating procedures. This enables their customers to assess, analyze and manage the inherent risk of partnering with them. Today we’re going to dive into the security response process and suggest a better approach.
While this may sound like a simple transaction, it’s far from a mere exchange of information. The size and complexity of a global business supply chain, and the volume of information that needs to be gathered from different places, is increasing over time.
Thousands of suppliers and service providers interact in a complex ecosystem with dependent and sometimes undisclosed processes. Understanding this network and the potential risks behind it poses a big challenge for organizations.
However, they keep using siloed systems and manual processes such as spreadsheet-based questionnaires, which are highly inefficient. Vendors need to answer the same questionnaires and requirements over and over again, while enterprises need to chase them every time they need a new assurance. These ad hoc, manual processes are costly and time-consuming.
What if there was a way to share verified vendor information to economize these processes and reduce workload redundancies?
The problems of traditional TPRM
From the vendor perspective, these are some of the biggest pain points:
- Manual steps in multiple applications
- Repetitive work answering the same questions over and over again
- Manual process to respond to due diligence requests via email
- Insecure and unreliable process – business owners might sometimes send outdated versions of security documents that they store locally, with the hopes of speeding up the sales cycle. Sometimes they might not involve the security team at all.
- Each customer has different formats and styles of due diligence processes, risk assessments, and collaboration for remediation. What is centralized and simplified for the customer can be a tangle of portals for the third-party.
- After due diligence, the vendor has to maintain the documentation across all customer portals.
From the enterprise (customer) perspective:
- Slow or unresponsive vendors, which leads to wasted time chasing them via email or phone
- Inconsistent methodologies
- Limited visibility into potential risk
- Difficulty in customizing assessments
- Inability to scale the assessment process as the company grows
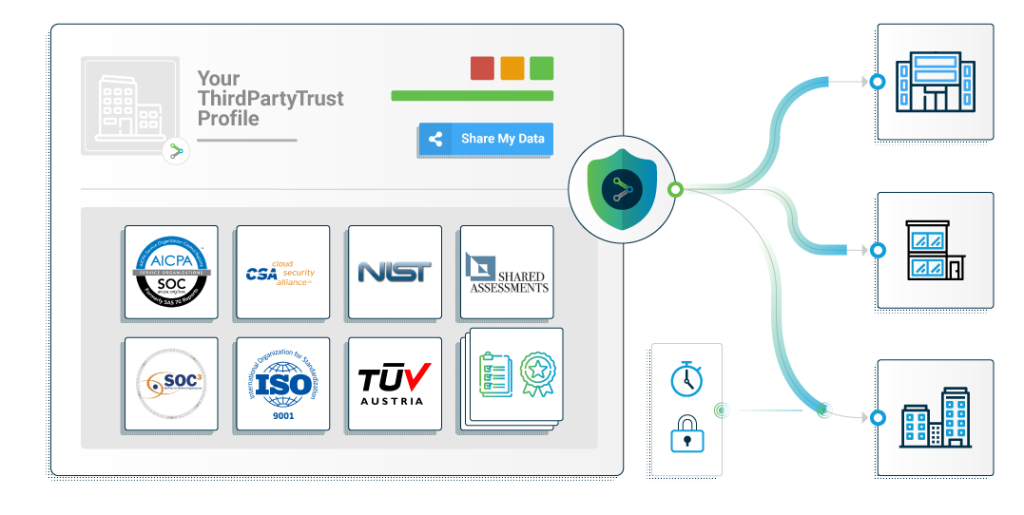
Introducing the Centralized Security Profile
Instead of focusing on 1:1 relationships, we think it’s time to create more agile partnerships.
A centralized security profile can significantly reduce time and costs for both the enterprise and the third-party. The benefits are clear:
Document Control
Vendors can store security and compliance documents in their profile, such as:
- SIG Lite
- ISO 27001
- SOC 2
- HITRUST
- MDS2
- Cyber-liability Insurance
- Penetration Testing
- HIPAA Attestation
Workflow Management
A network-enabled platform creates a streamlined process. In this case, for sharing security documents, ultimately cutting down the redundancies and inefficiencies involved in the due diligence process.
This reduces the turnaround as each third-party is onboarded once, and is then able to store and share its security documents extensively. New customers receive an invitation to view their profile after a quick registration in the selected platform.
Learn more: Beacon by ThirdPartyTrust: Scaling your Security Response Process
Sales process/cost
Reduction in questionnaire completion and sales cycle time can be as high as 70% using this self-service portal approach. To give an example, you could eliminate the cost of purchasing a SIG Lite, as it’s included in the license fee when purchased from ThirdPartyTrust.
Towards a Better Security Response Process
After listening to both sides of the third-party risk assessment/questionnaire review process, we at ThirdPartyTrust are modernizing TPRM for enterprises and their third-parties. Our network-enabled solution offers automation and workflow management for more streamlined processes and improved communication.
Enterprises can use our platform to reduce risk across industry supply chains and collaborate with their industry peers on assessing vendors in one common network. We band the good guys together creating a shared sense of transparency and insight into the supply chain.
At the same time, third-parties can build a centralized profile to easily share their security posture with their customers.
To learn more about how ThirdPartyTrust can help you manage third-party risk across your organization, request your free trial now:




