Kaseya Ransomware Attack: Lessons Learned on Digital Supply Chain Threats
The cybersecurity community was shaken last week after a massive supply-chain ransomware attack targeting managed service providers (MSPs) who use the Kaseya Virtual System Administrator (VSA). Attackers encrypted data at more than 1,000 companies and demanded an initial $70 million ransom to retrieve the files. Here’s what you need to know about the Kaseya ransomware attack.
The timeline of events —What happened?
July 2nd— Kaseya reported they were the victim of an attack exploiting their on-premise remote monitoring and management solution, VSA. The company quickly took SaaS services offline and warned customers not to run its software until a patch is available and manually installed.
It is believed that the threat actor is REvil/Sodinokibi, a ransomware-as-a-service (RaaS) affiliate. Automation allowed attackers to move from exploitation of vulnerable servers to installing ransomware on downstream companies faster than most defenders could react.
Researchers at Huntress Labs think the attack took two hours, so companies would have to run frequent monitoring and alerts to have caught the changes in their network. This means customers had very little to no time to detect and block the attacks.
Ransomware as a service (RaaS) is a subscription-based model by which affiliates use ransomware tools developed by others to execute ransomware attacks. They earn a percentage of each successful ransom payment.
July 3rd to 5th— Investigations continue to determine the root cause and remediate all the vulnerabilities. Kaseya spokesperson Dana Liedholm confirmed that the incident involved multiple vulnerabilities in the company’s products and called it a “sophisticated weaponized attack with ransomware”.
Huntress researchers confirmed that cybercriminals have exploited an arbitrary file upload and code injection vulnerability and presume an authentication bypass was used to gain access into these servers.
The ransom was lowered from $70M to $50M USD to publish a universal decryptor that can unlock all systems that have been affected by the file-encrypting ransomware.
July 6th & 7th— Kaseya plans to bring SaaS servers back online and release a patch but keeps pushing back the release date, presumably due to additional security checks and updates needed.
July 8th— Kaseya CEO Fred Voccola announced in a video that VSA SaaS and on-premises services would be back online Sunday, July 11th afternoon. This is four days later than the original date announced, following recommendations to add extra security measures to address all vulnerabilities leveraged in the attack. Voccola also announced plans to offer financial assistance for customers affected by the outage.
Among the affected organizations was the Swedish grocery chain Coop, which had to close several hundreds of stores on Saturday because of the ransomware attack, according to Reuters. As it turned out, its cash registers are run by Visma Esscom, which manages servers for a number of Swedish businesses and in turn uses Kaseya.
July 12th— Kaseya released the patch to VSA On-Premises customers and completed the restoration of services, with 100% of their SaaS customers live as of 3:30 AM US EDT.
Later on the same day, Kaseya announced unplanned maintenance with an expected downtime of 20 minutes. The release stated: “With the large number of users coming back online in a short window, we have seen some performance issues. We made some configuration changes to address and need to restart the servers for these to take effect and improve performance.”
Who owns the risk?
In a report from the Associated Press, Voccola said that he was confident that when an investigation is complete, it would show that not just Kaseya but also third-party software were breached by the attackers.
This raises, once again, the critical question: who is accountable for supply chain data breaches? This testimony seems to be heading in the direction of fourth-party risk and the idea that there’s always another link in the chain to point to when it comes to security incidents.
While that may be true, victims of data breaches almost always blame the company to which they trusted with their data, not their third party vendors. It’s a business responsibility to assess and secure all levels of information sharing with a third party vendor as part of a third party risk management (TPRM) program.
Kaseya ransomware attack, the latest case of supply chain attacks
The Kaseya attack underscores the danger that weaknesses in business supply chains pose to organizations. Experts suggested that it was launched during a holiday weekend (4th of July) to maximize impact and profit through the supply chain when business defenses are down.
Read more: 3 ways to boost your supply chain resilience
Kaseya and other remote monitoring and management (RMM) providers are ideal targets for supply chain attacks. Since the software is used by managed service providers, any compromise not only encrypts or locks systems and files at those firms, but also at their clients’ businesses.
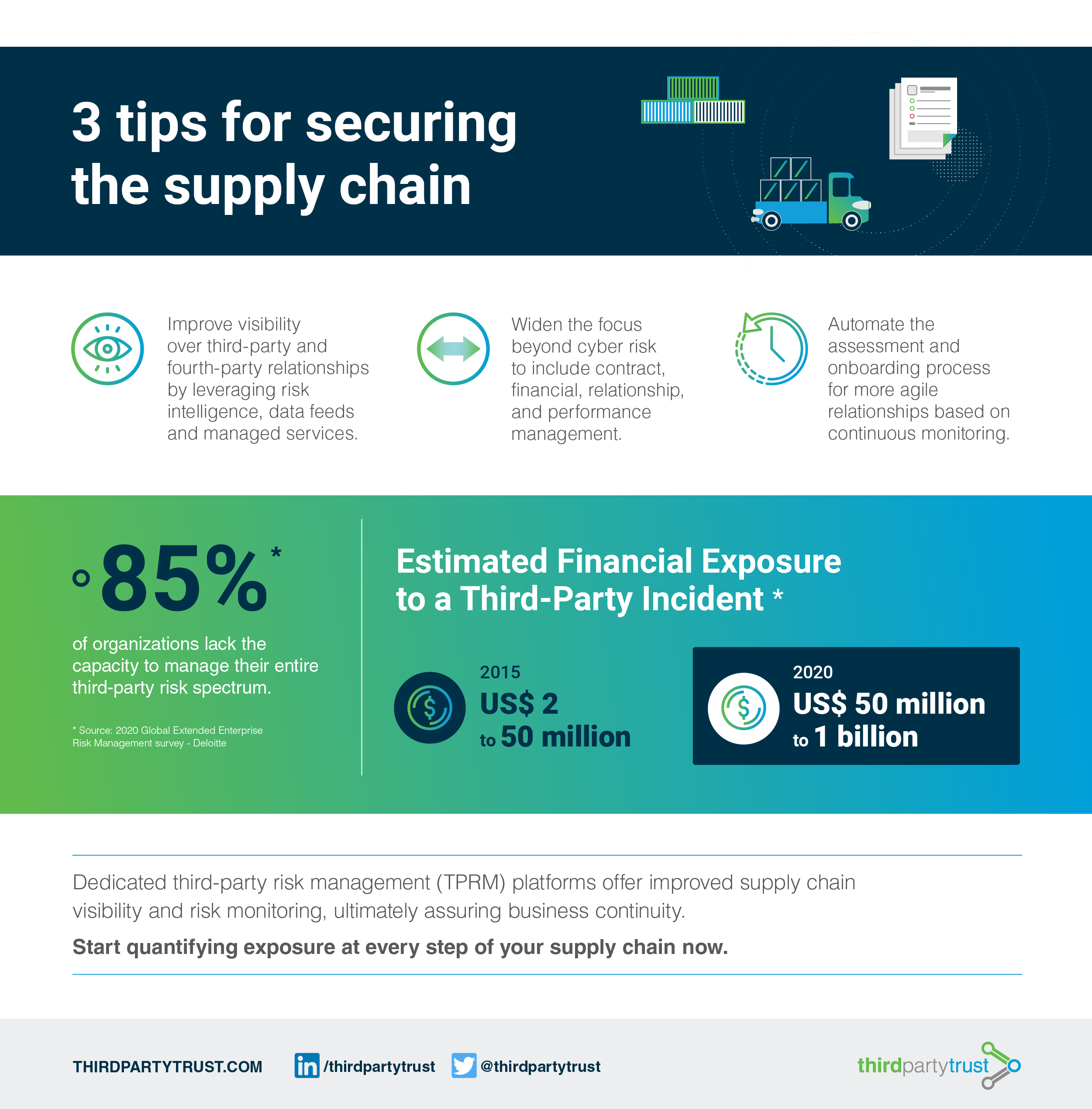
This infographic sheds light on supply chain attacks and how to protect against them (click on the image to enlarge):
Evidence shows that more than 70 managed service providers were impacted, resulting in more than 350 further impacted organizations. Kaseya’s CEO pointed out that only between 50-60 of the company’s 37,000 customers were compromised. But since 70% were managed service providers, the attack surface was expanded.
One lesson learned from this case is the importance of continuous monitoring: in less than two hours, attackers spread throughout a network of interconnected businesses and only a real-time continuous monitoring tool could have detected that movement.
A second lesson is the importance of assessing and monitoring the relationship with third party vendors with access to critical data or systems. Organizations can have hundreds or thousands of suppliers digitally connected, and the risks are rarely quantified, as supply chain cybersecurity is often a relegated part of the strategy. However, monitoring vendor risks and conducting a third party risk management strategy can be simplified given the right toolset.
In the world of cybersecurity, prevention goes a long way to avoid ending up in the headlines for the wrong reasons.
Securing your supply chain should be your next step.
Learn more about third party risk management (TPRM) and how ThirdPartyTrust can help you get started: