007 Life Lessons through the Verizon Breach Report: #1 Identity
When it comes to securing our enterprises, there’s so much to learn from a gadget wielding international crime-fighter like James Bond. Our CEO Anders Norremo and Jason Torres from Rush University Medical Center recently presented “007 Life Lessons through the Verizon Breach Report” in the 7th Annual Hacking Conference by ISACA and The Institute of Internal Auditors. Read on to step through these life lessons, how they relate to the data presented in the Verizon Data Breach Report, and how to apply them.
The data from the Verizon breach report helps us understand where the threats are, and what’s leading to breaches. That way we can take a risk-based approach to areas that need to be addressed. When it comes to third-party risk management, the question is what controls should you assess with your third-parties?
Lesson 1: Identity
Bond’s identity is unmistakable: just by seeing his silhouette you instantly know who he is. When we look at cyber, this becomes equally important. Always remember who you are!
Many of the breaches we commonly see involve some sort of identity hijacking or impersonation. Looking at the Verizon Data Breach Report we see the #1 and #2 actions that result in a breach (which is defined as an incident that results in a confirmed disclosure) are hacking and social attacks.
In the first case, broadly you must know the identity of the user, and in the second case you must know and verify the identity of the sender. Of course social attacks can also be dumpster diving or tailgating, but the most common by far is phishing.
The proliferation of SaaS (combined with the uptick in remote work during the pandemic) exacerbated the problem, as there are too many users getting into too many systems.
Pro Tip: While multifactor authentication is a best practice, it would be better to implement single sign on or some other form of company-wide identity and access approach. Centralization definitely eases this burden.
This brings us to Identity and Access Management (IAM), for which Gartner provides the following description:
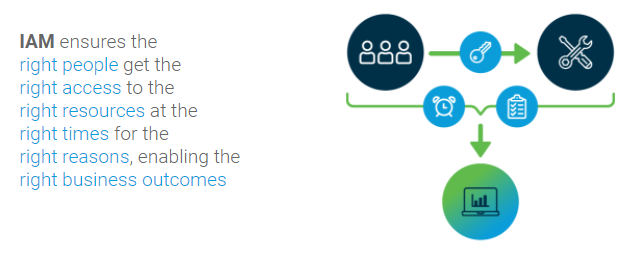
In our case (the ThirdPartyTrust platform to automate and streamline third-party risk assessments) this comes in the shape of custom privileges based on roles for personalized access and relationships between job titles, departments and roles.
While you’re usually responsible for provisioning users at each third-party, with ThirdPartyTrust, third-parties manage their own users and privileges. They receive their own free accounts to self manage once you’ve invited them into the platform, where they’re able to answer your security questions. All you need is a starting point of contact on their side, who will be able to invite more of their colleagues to complete your requirements. This ultimately removes the burden of access and user management from your team.
Why are stolen credentials a concern?
Attackers are more likely to use stolen or lost credentials than malware in their attacks, Verizon said in its Data Breach Investigations Report.
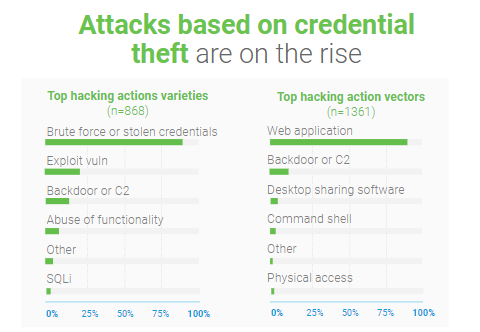
Malware infections dropped from almost half of all security breaches in 2016 to 22%, which is the lowest it has been in all the years the DBIR team has been tracking this statistic. Hacking —which includes brute-forcing passwords— remains the primary attack method at 45%, and social attacks —including social engineering— was found in 22 % of the reported incidents.
What is really eye catching is that inside the hacking category, we see that it’s dominated by stolen credentials and/or brute force attacks against web applications.
Why is this so important? In today’s changing landscape we are seeing a continued move to the cloud and each department of the business is becoming “SaaS-ified”.
What that means is that the attack surface is multiplying beyond the four walls of your business. Back to identity: how will you ensure that identity is being checked both inside your business as well as in the third-parties you are using?
This should be one of the most important questions to ask when you are assessing the security of your SaaS vendors.
How to make sure you know who’s who?
Centralizing your IAM function is going to be the key. Trying to make sure that your internal web applications and vendors can shut down logins via credentials would be one great example. If they can’t do that, maybe multi factor authentication can be enabled.
It’s becoming nearly impossible to manage hundreds or thousands of users across different applications. That’s why at ThirdPartyTrust, we’ve made it really easy for enterprises to manage the provisioning, de-provisioning and permissioning of accounts and privileges.
To learn more about how ThirdPartyTrust can help you streamline your TPRM program, request your free trial now:




