Building requirements is a core component of the security risk assessment process within a vendor risk management (VRM) program. In a nutshell, a requirement is a documented or functional need that a third party vendor needs to satisfy in order to comply with its customer’s risk assessment framework. However, the traditional, manual approach to VRM will often make it hard to customize requirements and will subject all vendors to the same set of questions.
Many organizations looking to fine-tune their security assessment process will want to dive into the role of custom requirements within a third party risk management program (TPRM). To that end, this blog provides an introduction to this process and explains how our latest ThirdPartyTrust feature takes requirement customization a step further.
The use of requirements in vendor risk assessments
A requirement can range anywhere from custom or industry standard questionnaires like SIG Core or SIG Lite, compliance with the PCI standard, an ISO certification, a pen test, or others.
There are different types of requirements, aimed at assessing the robustness of a vendor from different angles. After all, vendor risk management (VRM) is about evaluating the inherent risk of business partners, suppliers, or third party vendors to ensure they will not expose the organization to an unacceptable potential for cyber risk or business disruption. This assessment takes place before a business relationship is established as part of the due diligence process, and continues throughout the duration of the business contract.
While the usual requirements in third party risk assessments include industry questionnaires, certifications, and attestations, organizations might sometimes build their own custom requests based on their risk appetite.
These can fall into different categories related to information security, governance, and compliance, such as:
- Architectural requirements, to understand the integration ecosystem and the system architecture of the vendor, and how robust is their infrastructure.
- Business requirements, as a high-level understanding of the vendor’s goals and business model.
- Reliability or service quality requirements, describing the conditions under which the service provided by the vendor must remain effective, the qualities it must have, or constraints within which it must operate.
- Regulatory requirements, defined by laws (Federal, State, Municipal, or Regional), contracts (terms and conditions), or policies (company, departmental, or project-level).
But how can organizations most efficiently integrate all these data points into the actual assessment process?
Building requirements for security risk assessments in ThirdPartyTrust
ThirdPartyTrust is a third party risk management (TPRM) workflow management, document repository and process automation platform. Our tools are designed to help you collect the right information and ask the most appropriate questions based on your vendors’ inherent risk to your organization.
To that end, you can build requirements within your assessments through different rules. These rules allow you to request specific information from third party vendors based on your needs and expectations.
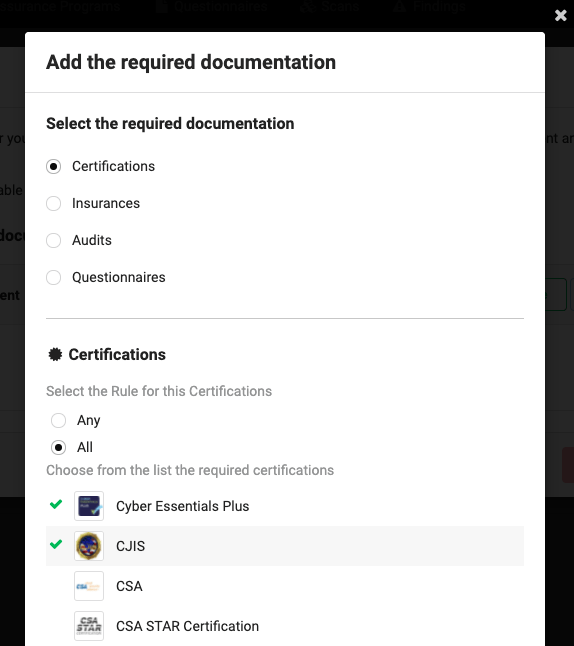
Creating requirements in our platform is a simple process, where you select the required documentation (certifications, insurances, audits or questionnaires) and configure the criteria that will be used to assign these requirements to your vendors. For example, their tier or label used in your risk management dashboard, or their score in a certain risk category. Organizations usually categorize their vendors based on the criticality of the services they provide and the potential impact on the business.
For each type of documentation you can determine if all documents are required, or at least one document of that category is to be provided. As you can see below, within the certifications category, you can choose from a list of required certifications, such as Cyber Essentials Plus, CJIS, CSA, or CSA STAR.
But there’s more.
We always say one size does not fit all when it comes to third party risk management, so organizations need the ability to customize their evaluation. Requirements vary according to the type of relationship and business outcome. If the vendor to assess will be a data controller for CCPA and GDPR, they might need to show their insurances, policies, pentests, questionnaires, etc. If they’re handling credit cards, they might also need to show their PCI compliance, but an ISO certification might not be necessary. These are just some examples, but the possible combinations are infinite.
Whereas a manual approach with emails and spreadsheets might make it difficult to customize the requirements, requiring duplicate files or creating separate tabs; A streamlined, automated process will make this smooth on both ends, making sure both enterprises and their third parties request and send only what they need and eliminating repetitive efforts.
We’ve previously discussed why this manual approach is a bad idea and why building a centralized security profile is the way to modernize vendor risk assessments once and for all – for both sides.
To make this customization experience even better, ThirdPartyTrust allows you to include alternate requirements in case the vendor marks any elements as not available. Sometimes they might not be mature enough to comply with some of your requirements, or sometimes they might need a little more time to get a hold of a certain document. In those cases, the ability to swap and present an alternative document will come in handy to make the assessment move forward.
As you can see, building custom requirements is essential to the success of your security risk assessment process. Are you ready to get started?