What’s the cost of a data breach in 2022?
IBM released the Cost of a Data Breach Report 2022, which provides insights into the financial impact of data breaches across industries. Here’s what you need to know to protect your organization.
What is a data breach?
A data breach is the compromise and subsequent release of private or confidential information to unauthorized parties. It can result in the data being copied, transmitted, stolen, or used with other malicious intentions.
What is the cost of a data breach?
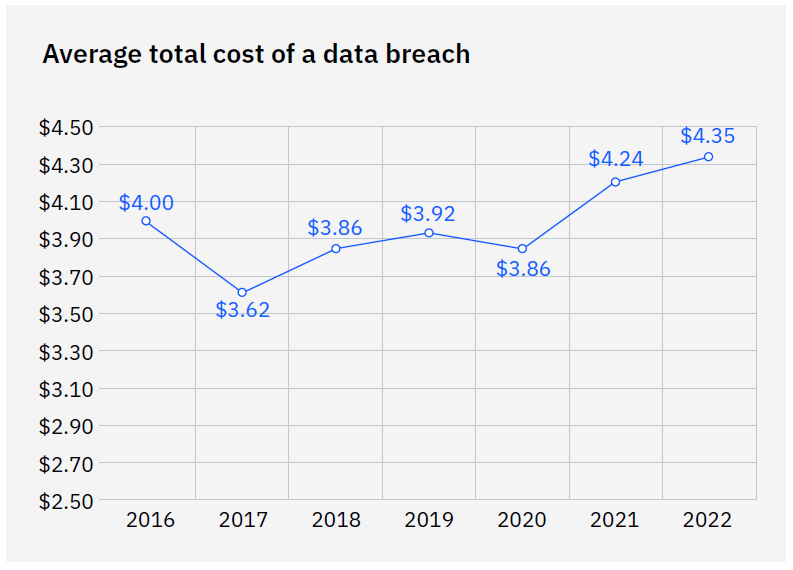
The average total cost of a data breach is $4.35 million. In critical infrastructures, it rises to $4.82 million —this means organizations in the financial services, industrial, technology, energy, transportation, communication, healthcare, education and public sector industries.
Reaching an all-time high, this figure represents a 2.6% increase from last year, when the average cost of a breach was $4.24 million. The number has climbed 12.7% since the 2020 report.
Source: IBM Cost of a Data Breach 2022
Tech giant T-Mobile has recently agreed to pay customers US$350 million to settle multiple class-action suits stemming from a data breach disclosed last year, affecting tens of millions of customers. Target and Home Depot are other examples of costly settlements, which can also cause regulatory and reputational damage.
Read more: Top 5 costliest breach settlements
How does the cost of a data breach vary by country or region?
The top five countries and regions for the highest average cost of a data breach were the United States at $9.44 million, the Middle East at $7.46 million, Canada at $ 5.64 million, the United Kingdom at $5.05 million, and Germany at $4.85 million.
The United States has led the list for 12 years in a row, while the fastest growing country is Brazil, with a 27.8% increase this year from $1.08 million to $1.38 million.
How does the cost of a data breach vary by industry?
Data breaches in the healthcare industry have been the most expensive for 12 years, increasing by 41.6% since the 2020 report. This year, they hit a new record high, with an average breach costing $10.10 million.
Financial organizations had the second highest costs — averaging $5.97 million — followed by pharmaceuticals at $5.01 million, technology at $4.97 million, and energy at $4.72 million.
What is the cause of a data breach?
The use of stolen or compromised credentials remains the most common cause of a data breach, as per IBM’s research. Stolen or compromised credentials were the primary attack vector in 19% of breaches in the 2022 study, and also the top attack vector in the 2021 study, having caused 20% of breaches.
Watch on demand: Stolen credentials, a conduit into your network
These breaches had an average cost of US$ 4.50 million, and the longest lifecycle — 243 days to identify the breach, and another 84 days to contain the breach.
The second most common cause of a data breach is phishing, accounting for 16%. It is also the costliest, averaging US$ 4.91 million in breach costs.
In critical infrastructure organizations, 28% experienced a destructive or ransomware attack, while 17% experienced a breach because of a business partner being compromised.
Read more: Everything to know about third party data breaches
Can security measures prevent data breaches?
No organization is bullet-proof, but multi-layered strategies with robust security mechanisms and dedicated technology can drastically reduce the impact and cost of a data breach. In particular, the report analyzed:
- Security AI and automation
- Zero Trust
- Incident Response Plans
- Extended detection and response (XDR) technologies
Breaches at organizations with fully deployed security AI and automation cost US$3.05 million less than breaches at organizations with no security AI and automation deployed. These companies also experienced on average a 74-day shorter time to identify and contain the breach, known as the breach lifecycle, than those without security AI and automation — 249 days versus 323 days.
Zero trust is another mechanism that makes the difference. The 59% of organizations that don’t deploy a zero trust architecture incur an average of US$1 million in greater breach costs compared to those that do deploy.
Read more: Zero Trust —How to secure network access
Among critical infrastructure organizations, an even higher percentage of 79% doesn’t deploy zero trust. These organizations experienced on average US$5.40 million in breach costs, more than US$1 million higher than the global average.
Having an incident response team and/or plan that was regularly tested led to significant cost savings as well. Businesses saw an average of US$2.66 million lower breach costs than organizations without an incident response team or plan. The difference of US$3.26 million versus US$5.92 million represents a 58% cost savings.
44% of organizations implemented extended detection and response (XDR) technologies, which allowed them to save 29 days in response time. Specifically, organizations took 275 days to identify and contain a breach with XDR deployed, versus 304 days without XDR deployed. This figure represents a 10% difference in response times.
What is the data breach lifecycle?
The data breach lifecycle is the time elapsed between the first detection of the breach and its containment, as defined by IBM. Identification means detecting that an incident has occurred, while containment means resolving a situation when it’s been detected and ultimately restoring service.
How long does it take to identify and contain a data breach?
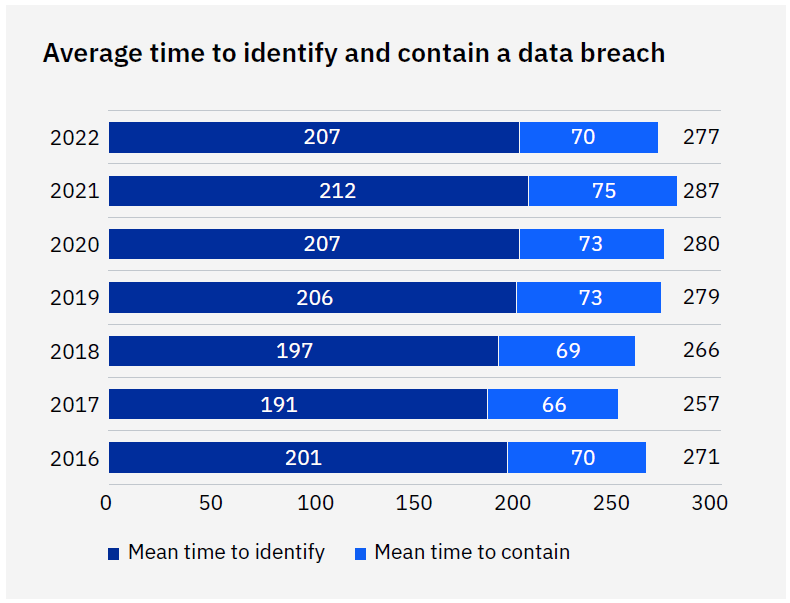
The average time to identify and contain a data breach fell from 287 days in 2021 to 277 days in 2022, a decrease of 10 days or 3.5%.
Source: IBM Cost of a Data Breach 2022
The 277-day average in 2022 means that if a breach occurred on January 1, it would take until October 4 of that year to be identified and contained.
Read more: Victim of a data breach? A 10 step guide to getting back on track
Are data breaches recurring?
83% of organizations in IBM’s study have experienced more than one data breach. Of the 550 organizations surveyed, just 17% said this was their first data breach.
“With security teams handling more incidents every year and considering the impact of remote work on security, it’s likely the recurrence of breaches is climbing.”, states the report.