Risk Assessments: How To Reduce Friction Between Sales and Security
If you are selling software or any type of service to other businesses, most of your customers will ask you to complete a security assessment. While necessary for companies to outsource safely, they can be extensive and time consuming, with hundreds of questions on spreadsheets and long email threads. This often creates friction between sales and security, ultimately slowing down the business.
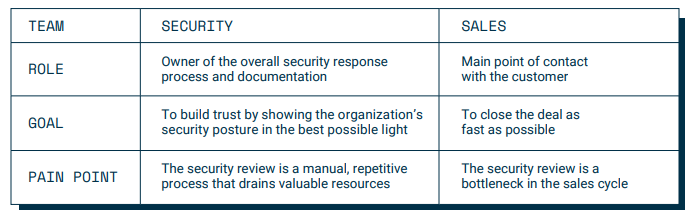
For the sales team, the process of responding to security reviews is a bottleneck in the sales cycle. For security, it’s a drain of resources to answer the same questions and share the same documents over and over again, but they need to own the process so customers can get the right documentation. So how to make them work together and reduce friction?
The Struggles of the Security Review Response Process
The vendor security response process–by which companies who act as third party vendors respond to requests for assurances of their security practices–is rarely a straightforward process.
If your business is on the receiving end of a VRM or TPRM (vendor risk management or third party risk management) request, these questions may sound familiar:
- How much time does your team spend responding to one-off security questionnaires?
- How many times were you asked for a SIG Lite or a pen test this year?
- How much time is spent waiting for an NDA to be signed?
For years, the process of assessing and representing third party risk has been as manual and repetitive as it has been necessary to do business in the modern world.
As a result, security teams like yours spend valuable resources answering gigantic spreadsheets with questions every week. These questionnaires range anywhere from 40 to 400 questions to assess your security policies and procedures, which is a compliance mandate for enterprises, but a killer for any small to medium-sized GRC team.
Download Vendor Cheat Sheet: Do’s and Don’ts of Answering Security Reviews
With the aim of speeding up the deal, Sales staff might want to step in and share the documentation themselves, often at risk of sharing an outdated version or the wrong file. They might see the security review as a stopper in the sales cycle and therefore want to bypass any delays.
Meanwhile, Security wants to be as accurate as possible, but faces the time-consuming task of answering one-off security questionnaires over and over again. In addition, there’s a challenge around ownership: Where do (or should) the already answered security questionnaires sit? Who should be tasked with updating them and/or personalizing them for a particular deal?
This approach is impossible to scale, as there’s a limit in the amount of questionnaires the same people can answer on a weekly basis.
Reducing Friction Between Sales and Security
Like with many other challenges of interconnected supply chains, technology can help. There are solutions and best practices available for you to simplify and scale your security response process while overcoming the most common struggles that plague TPRM and cause friction.
If one of the biggest issues is the repetitive nature of this process, with security starting from scratch on every assessment, automation presents itself as the ultimate solution.
Imagine if you could proactively and automatically share what was already answered or filled out in a previous, similar assessment. Reusing your security answers and assurances can streamline your response process so resources can be used efficiently.
How to begin leveraging automation? The first step is to assemble a robust security profile in one place, so the usual documents and answers to common questionnaires are centralized and easy to track. This includes:
- SIG Core and Lite, Cloud Security Alliance CAIQ, CIS Controls, NIST, and other questionnaires
- SOC reports, ISO certifications, HiTrust and many others
- Penetration tests, application scans, and other attestations
- NDAs, insurance documentation, and other audits
Learn more about the ThirdPartyTrust Centralized Security Profile for Third Party Vendors
This approach could solve all the frequent issues causing friction between sales and security. With a centralized security profile:
☑ Ownership is distributed so that every person on every team can access the same up-to-date information
☑ Time-dependent constraints are minimized as common responses are collected in one space and previous assurances are automatically updated
☑ Trust and reputation is established quickly and consistently as the profile can be instantly shared with prospective customers
See how ThirdPartyTrust can help you build a scalable process to comply with security reviews:
Towards a Better Approach to Vendor Risk Assessments
Based on testimonials from our customers using this approach, like Vertafore, Netskope, Spiff, and Hoxhunt, the due diligence response can take just one business day instead of weeks or months and reduce the workload by up to 95%.
Explore Case Studies on How To Reduce the Security Review Response
Time is a major hurdle, but a vast majority of the problems faced by security teams in organizations who act as third party vendors can be solved through automation. It’s time to leverage processes and technology that eliminate repetition, decrease internal friction, and increase oversight and control.
If you’re ready to explore automation and building a centralized security profile, we can help. Talk to an expert today.

A Practical Guide to Faster Compliance
Rising regulatory pressure is coupled by increasing concerns about third party risk, forcing vendors to show a robust security posture up front.
This strategy guide explains how to simplify compliance with security reviews by automating the most common questionnaire responses and centralizing security documentation to reduce friction between sales and security.